TunHub Integration
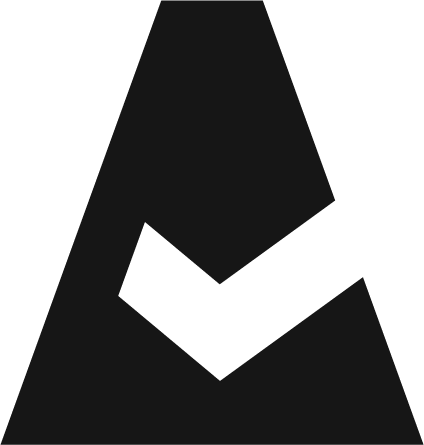
TunHub is a Cloudaware-managed proxy integration designed to ensure a secure connection between customer local network resources and Cloudaware CMDB. This guide explains how to set up TunHub in Cloudaware.
 To see the TunHub integration in action, request a demo.
To see the TunHub integration in action, request a demo.
Introduction
To enable the Cloudaware CMDB collector to discover infrastructure in a private network, deploy a local proxy. The local collector proxy requires ingress access to the target endpoint and egress access to the Cloudaware TunHub server.
You can deploy the proxy configuration to any Breeze agent that meets the requirements. Up to two Breeze agents – active and standby – can be designated to support a single endpoint connection.
Customers can set up the TunHub integration through a self-service interface in the Cloudaware Admin panel.
Set up Breeze
Select an existing server or provision a new one that has access to resources in the private network and can communicate with Cloudaware. Then install the Breeze agent:
Log in to Cloudaware → Admin.
Find Breeze in DevOps integrations → click 1 CONFIGURED.
Select the desired version and download the agent.
Install the Breeze agent on a server that meets the requirements:
Operating System: Linux onlyUbuntu 14 and newer
CentOS/RedHat/Oracle Linux 6–9
Debian 9 and newer
Amazon Linux (note that Amazon Linux 2023 is currently not supported for TunHub)
CPU: 1 core
Memory: Minimum 256 MB
Storage: Minimum 200 MB
Ports:Outbound TCP 443 to
breeze-server.cloudaware.com(for the Breeze agent)Outbound TCP 443 to
tunhub.cloudaware.com(for TunHub)
Once Breeze is installed, the server gets access to
breeze-server.cloudaware.comand may act as TunHub proxy.
Configure TunHub
Create a tunnel
Create a tunnel to grant Cloudaware access to private network resources. A tunnel must include at least one route.
Log in to Cloudaware → Admin.
Find TunHub in DevOps integrations. Click +ADD.

Fill out the form:
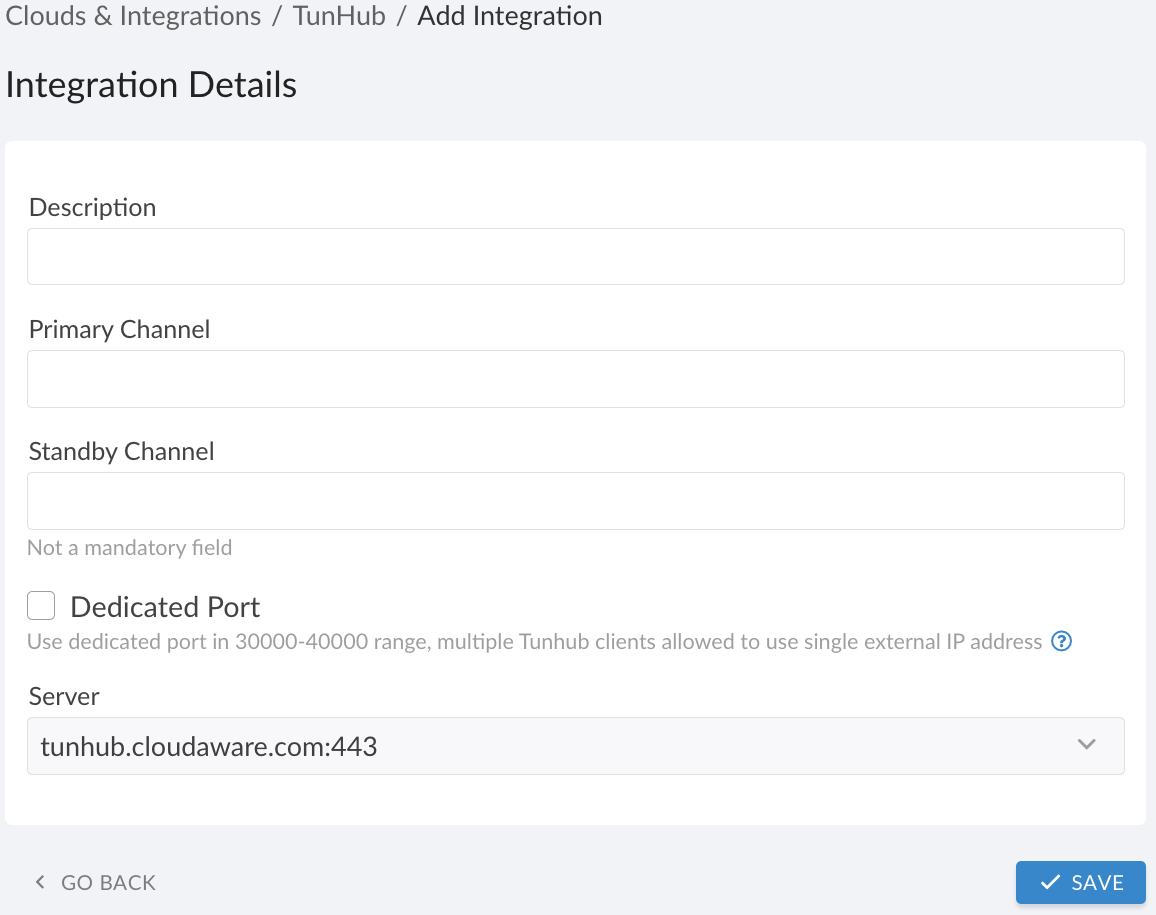
WHERE
Description – a descriptive name for this integration
Primary Channel – Breeze Agent ID* of the Breeze agent installed on the host. Note: This field cannot be edited later, so verify its accuracy.
Standby Channel (optional) – Breeze Agent ID* of the Breeze agent installed on the standby host. If the Primary Channel is unavailable, the Standby Channel is used until the Primary Channel is restored.
Dedicated Port – check this box if unique public source IP addresses for all egress TunHub connections cannot be provided. TunHub assigns a dedicated port from the30000-40000range (ensure the firewall allows outbound connections on this range). If not selected, TunHub uses port443and expects the connection to originate from a unique public IP address.
*To locate the Breeze Agent ID, use the CMDB Navigator in Cloudaware. Identify the server using either a specific list view or the general search. Open the server record and check the 'Breeze Agent' field. For Azure Virtual Machines, use the value from the 'VM ID' field instead.
Note that Breeze Agent ID formats vary by server type:
AWS EC2 Instance – i-XXXXXXXXXXXXXXXXX (=Instance ID)
Azure Virtual Machine – XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX (=VM ID)
Azure VM Scale Set Instance – XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX (=VM ID)
vCenter Virtual Machine – vcenter_XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX_vm-1111111 (=vCenter ID_Virtual Machine External ID)
Google GCE Instance – 1111111111111111111 (=Google ID)
Physical Server – ipXX.XX.X.XX_macXXXXXXXXXX (=Name)
Primary and Standby Channels must have different public IP addresses.
Click SAVE to test the connection.
Review the integration status. The yellow status light for Primary Channel means TunHub is waiting for Breeze to connect.
Configure routes
Each TunHub tunnel must have at least one route. A route maps a private network address to a Cloudaware-accessible address and generates an alternate address for integrations requiring a secure connection.
Open the three-dot menu → Edit Tunnel & Routes.
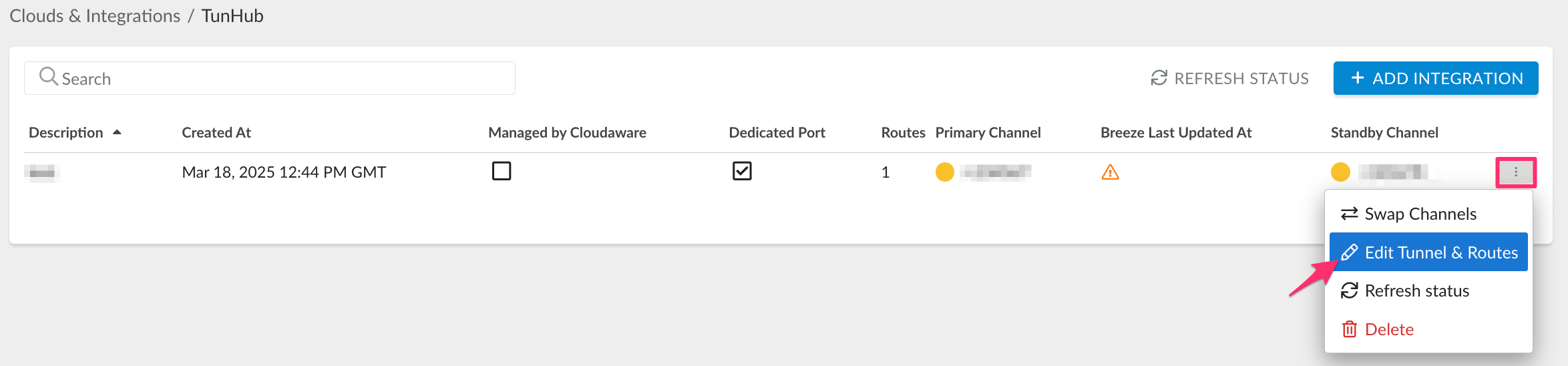
Click +ADD ROUTE.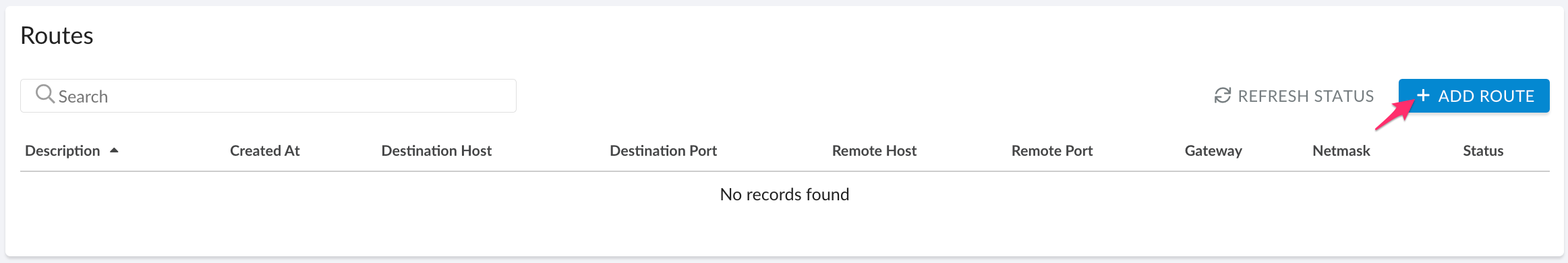
Each private network resource requires a unique designated route to be configured in Cloudaware TunHub.
Fill out the form:
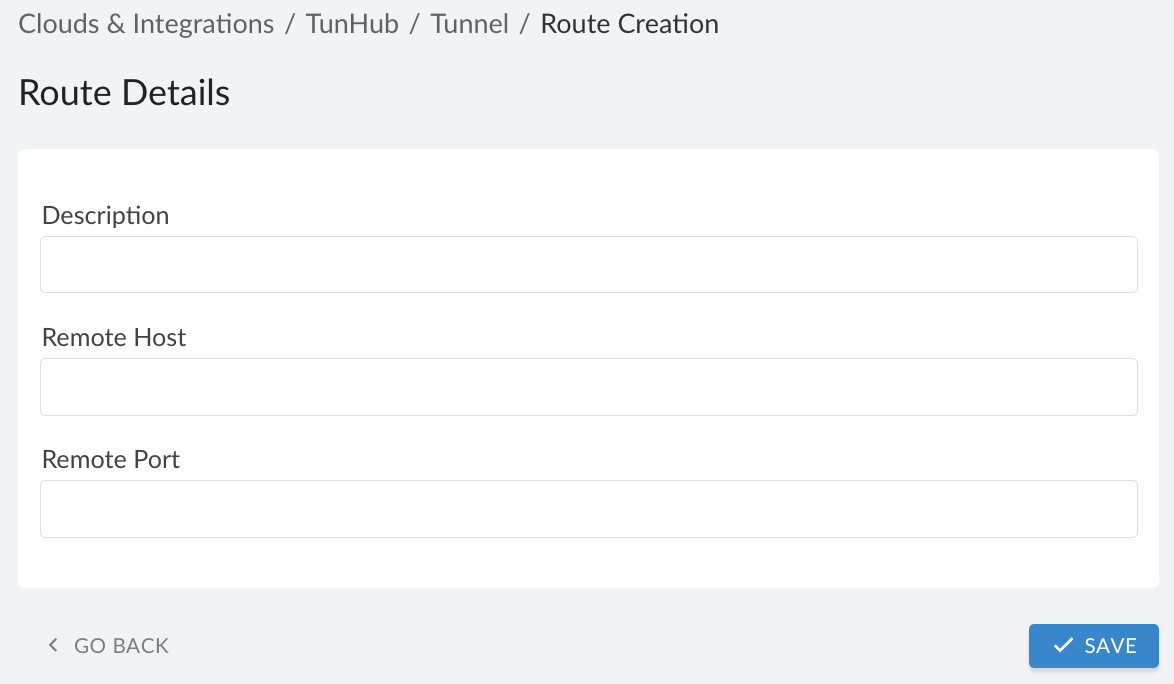
WHERE
Description – the route name (same as resource name, e.g., Jira)
Remote Host – the domain name or IP address of the resource in the private network
Remote Port – the resource port, typically443Click SAVE. Allow time for the route to reach green status, then proceed.
Once the route is pre-configured and ready, use the generated Destination Host and Destination Port values when configuring integrations.
For example:
Integration name | Destination Host/Port examples |
|---|---|
URL (e.g. | |
Host (e.g. | |
URL (e.g. Note that port | |
URL (e.g. |
Go back to the integration details. A green light in the ‘Primary Channel’ column indicates successful configuration. If the light is red, contact support@cloudaware.com.
If the box 'Managed by Cloudaware' is checked, the tunnel and routes cannot be edited or deleted by customers.
