Vulnerability Scanning - Overview
This page provides an overview of Cloudaware’s Vulnerability Scanning capabilities.
About
Cloudaware Vulnerability Scanning as a Service (VSaaS) is a comprehensive, low-friction, high-value security scanning solution. Vulnerability data is accessible directly within the Cloudaware CMDB.
Supported Scan Types
The following scan types are supported by Cloudaware:
Agent-Based Vulnerability Scans (Default)
Standard
PCI DSS (Windows and Red Hat only)
IP-Based Network Scans (Optional)
Standard
Standard Credentialed
PCI DSS (Windows and Red Hat only)
URL Scanning
OWASP Top 10 vulnerability scanning
Docker Image Scanning
Compliance Benchmarks
CIS Level 1, Level 2, and Custom
DISA
HIPAA Windows Audit
PCI DSS (Agent and IP-based)
SCAP
OVAL
MSCT
Vulnerability-Specific Scanning
BadLock
Bash Shellshock
DROWN
Intel AMT Security Bypass
Shadow Brokers
Spectre
Meltdown
WannaCry (Ransomware)
Other Capabilities
Patch Audit
Malware Detection
Mobile Device Discovery
Host Discovery
Scan Frequency and Scheduling
All scans are performed at least once every 7 days. The Cloudaware VSaaS algorithm automatically selects the optimal time to scan each asset. Customers may request on-demand scans at any time.
If a scanning agent is uninstalled or impaired, Breeze automatically performs a clean uninstall, repairs the agent if necessary, and reinstalls it.
CMDB Integration
Each Configuration Item (CI) in the CMDB includes a Last Scan Date field. Using CMDB reporting and workflow functionality, customers can:
Generate reports identifying unscanned assets
Create workflows to handle unscanned asset notifications
Each CI also includes fields indicating the number of Critical, High, Medium, and Low risk vulnerabilities associated with the asset.
Vulnerability data is accessible directly in the CMDB.
Customers can create workflows triggered when vulnerabilities are discovered or remediated.
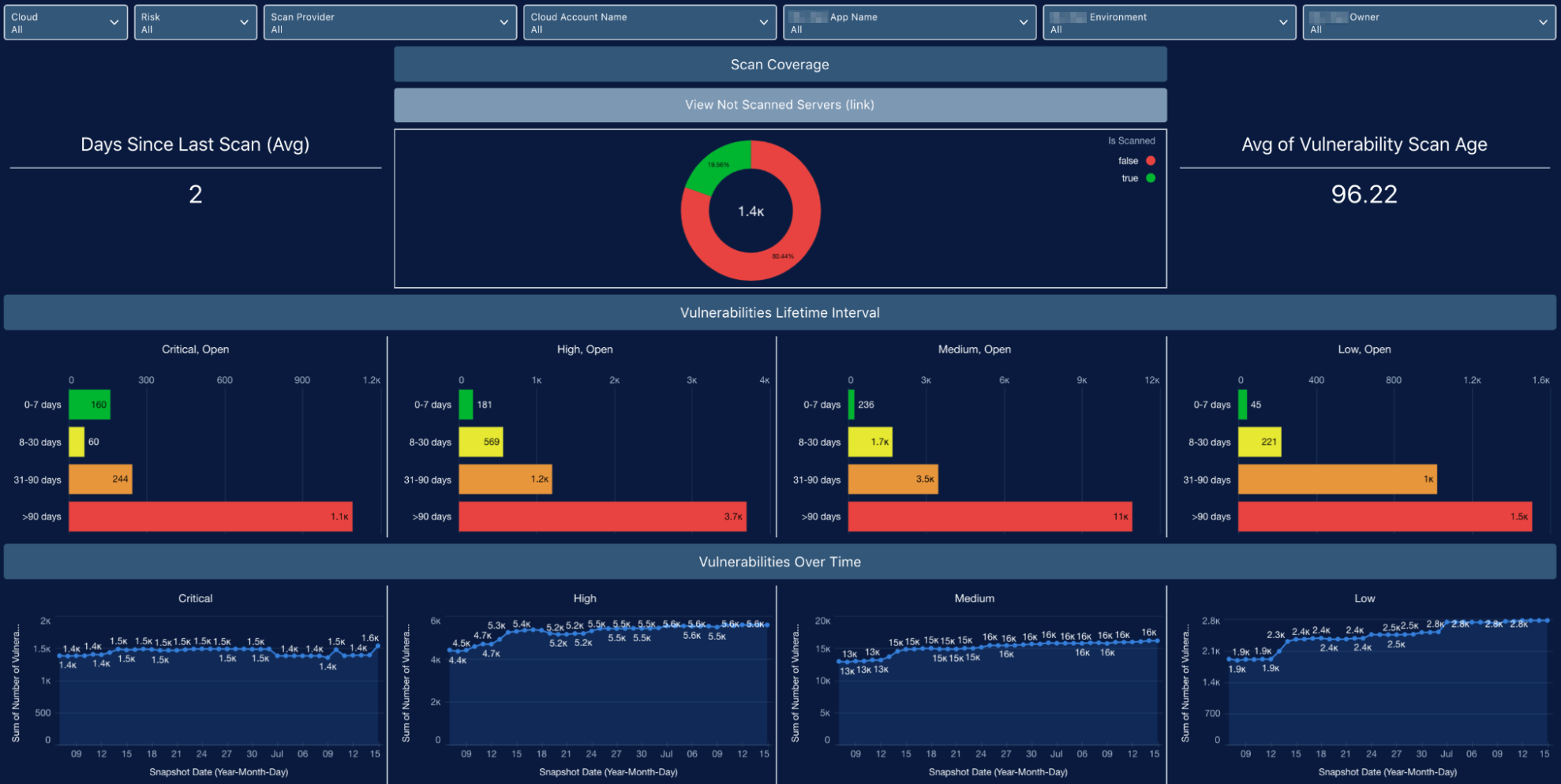
Customers can build dashboards tracking KPIs such as scanning coverage and vulnerability age.
Customers can generate reports showing assets that are not being scanned or that have critical vulnerabilities exceeding a defined age.
Customers can create CVE-specific reports identifying assets vulnerable to particular CVEs.
Using Cloudaware CMDB reporting, dashboarding, and advanced analytics, customers can review KPIs (for example, scanning coverage and vulnerability age), track assets affected by specific vulnerabilities or CVEs, and monitor vulnerabilities over time.
Ticketing and Incident Management Integration
Cloudaware VSaaS integrates with external systems such as ServiceNow, Jira, and PagerDuty.
Stateful ticketing integration is supported, meaning tickets are not only created in external systems but are also automatically updated when vulnerabilities are remediated.
List of supported objects
Cloudaware supports the following scanning-related objects (with API names):
CloudAware Scan Server
CA10__CaNessusPhysicalServer__cCloudAware Vulnerability Scan
CA10__CaNessusVulnerability__cCloudAware Vulnerability Scan CVE
CA10__CaNessusVulnerabilityCve__cDocker Runtime Vulnerability
CA10__CaDockerRuntimeVulnerability__c
