Creating Custom Role in Microsoft Azure
This guide explains how to create a custom role with extra permissions for Cloudaware in Microsoft Azure. To create custom roles, you must have the Owner or User Access Administrator role in Azure.
Create role for Storage Account keys access
The Azure built-in role Reader doesn't provide access to Storage Account keys, which are required to collect data about VHDs. Create a custom role with necessary permissions:
1. Log in to the Azure portal. Select a subscription or resource group where the custom role will be assigned.
2. Navigate to ‘Access control (IAM)’. Click Add → Add custom role. Name the role Cloudaware Custom Policy.
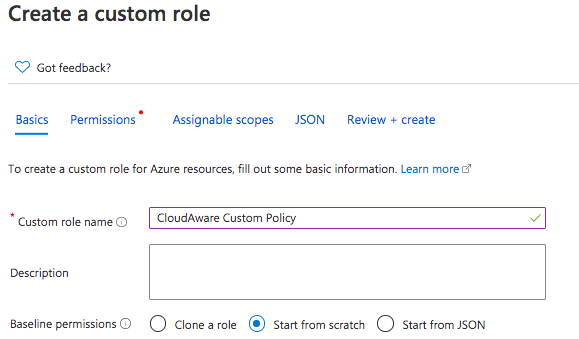
3. Choose one of the following options:
a) 'Start from scratch'.
On the ‘Permissions’ tab, select Add permissions. Copy and paste Microsoft.Storage/storageAccounts/listKeys/action in the Search for a permission box to select Microsoft Storage.
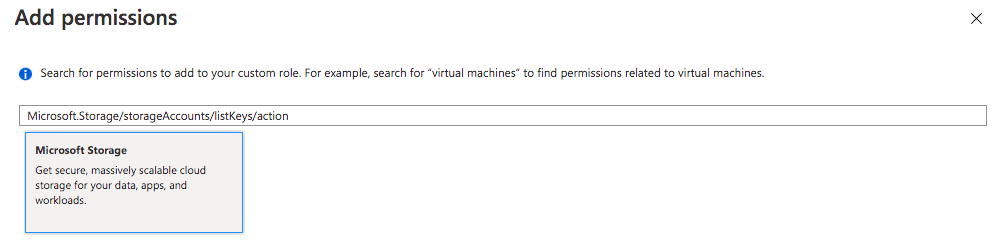
Check the box near the permission.
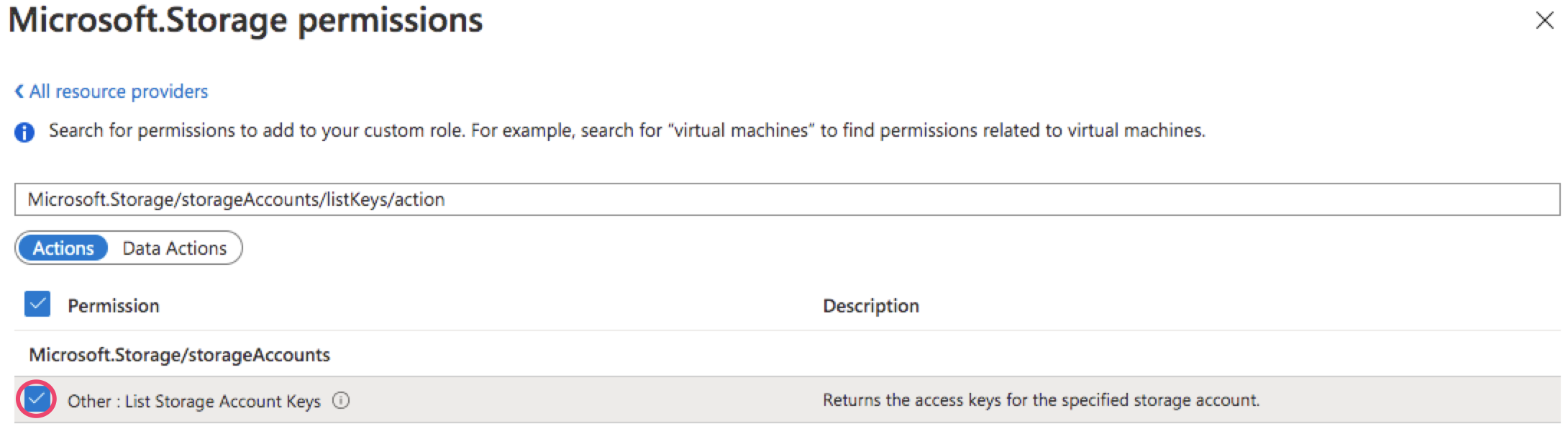
Click Add.
The permission Microsoft.Storage/storageAccounts/listKeys/action grants 'read' access to Storage Account Keys.
If you plan to install Breeze Agent, the permission Microsoft.Compute/virtualMachines/extensions/write is required for this custom role as well.
b) 'Start from JSON'.
Create a JSON file using the following template. Replace {subscription_id} with your Azure subscription ID.
{
"IsCustom": true,
"Name": "CloudAware Collector Extended",
"Description": "For collecting data about Blob Containers and VHDs we need to get access to the Storage Account keys as the default role Reader does not provide API access to these keys.",
"Actions": [
"Microsoft.Compute/virtualMachines/extensions/write",
"Microsoft.Storage/storageAccounts/listKeys/action"
],
"notActions": [],
"assignableScopes": [
"/subscriptions/{subscription_id}"
]
}c) 'Clone a role'.
Select an existing* role to clone.
*Common Azure built-in roles:
Built-in Role | ID |
|---|---|
Reader |
|
Contributor |
|
Virtual Machine Contributor |
|
Virtual Network Contributor |
|
Storage Account Contributor |
|
Web Plan Contributor |
|
SQL server Contributor |
|
SQL DB Contributor |
|
To modify permissions, open the ‘JSON’ tab, and update the JSON as needed.
The JSON body of the existing role should look like in the template below:
{
"properties": {
"roleName": "{your-role-name}",
"description": "",
"assignableScopes": [
"/subscriptions/{subscriptionId_1}",
"/subscriptions/{subscriptionId_2}",
"/subscriptions/{subscriptionId_3}"
],
"permissions": [
{
"actions": [
"Microsoft.Compute/virtualMachines/extensions/write",
"Microsoft.Storage/storageAccounts/listKeys/action"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}Replace {your-role-name} with your custom role name, and {subscriptionId_1}, {subscriptionId_2},{subscriptionId_3} in the section "AssignableScopes" with your subscription IDs. You can add multiple scopes if needed.
4. Assign the role:
If you're adding a native application, assign the custom role to a user.
If you're adding a web app/API, assign the custom role to the application.
Creating a custom role is an asynchronous operation. It may take some time for the role to become available.
5. Open the ‘Review + create’ tab, check the details, and click Create.
Create role for Azure App Service Config Settings access
Create a custom role to grant Cloudaware access to Azure App Service Config Settings:
Log in to the Azure portal -> Subscriptions.
Select a subscription. Navigate to ‘Access control (IAM)’ -> Roles. Click + Add -> Add custom role.
In the ‘Basics’ tab, set a name and description for the custom role. For baseline permissions, select Start from JSON.
Use the following JSON template:
CODE{ "properties": { "roleName": "{your-role-name}", "description": "{your-role-description}", "assignableScopes": [ "/subscriptions/{subscription-id}" ], "permissions": [ { "actions": [ "Microsoft.Web/sites/config/list/Action", "Microsoft.Web/sites/Read" ], "notActions": [], "dataActions": [], "notDataActions": [] } ] } }
WHERE replace {your-role-name}, {your-role-description} and {subscription-id} with values from your Azure environment.
Assign the role:
If you're adding a native application, assign the custom role to a user.
If you're adding a web app/API, assign the custom role to the application.
Open the ‘Review + create’ tab, check the details, and click Create.
Create role for tagging
Create a custom role to provide Cloudaware with permissions for tagging Azure resources:
Log in to the Azure portal -> Subscriptions.
Select a subscription. Navigate to ‘Access control (IAM)’ -> Roles. Click + Add -> Add custom role.
In the ‘Basics’ tab, set a name and description for the custom role. For baseline permissions, select Start from JSON.
Use the following JSON template:
CODE"properties": { "roleName": "{your-role-name}", "description": "{your-role-description}", "assignableScopes": [ "/subscriptions/{subscription-id}", ], "permissions": [ { "actions": [ "Microsoft.Resources/subscriptions/tagNames/read", "Microsoft.Resources/subscriptions/tagNames/write", "Microsoft.Resources/subscriptions/tagNames/delete", "Microsoft.Resources/subscriptions/tagNames/tagValues/read", "Microsoft.Resources/subscriptions/tagNames/tagValues/write", "Microsoft.Resources/subscriptions/tagNames/tagValues/delete", "Microsoft.Resources/subscriptions/resourceGroups/read", "Microsoft.Resources/tags/write", "Microsoft.Resources/tags/delete", "Microsoft.Resources/tags/read" ], "notActions": [], "dataActions": [], "notDataActions": [] } ] }WHERE replace
{your-role-name},{your-role-description}and{subscription-id}with values from your Azure environment.Assign the role:
If you're adding a native application, assign the custom role to a user.
If you're adding a web app/API, assign the custom role to the application.
Open the ‘Review + create’ tab, check the details, and click Create.
Update existing Cloudaware custom policy
Cloudaware may introduce new capabilities that require additional actions and permissions. If a custom role is already in place, it can be updated once across all subscriptions. Cloudaware Technical Account manager will provide the instructions.
Creating a custom role is an asynchronous operation. It may take some time for the role to become available.
