Amazon EKS Cluster Access for Cloudaware
This guide explains how to provide access to Amazon EKS Cluster for Cloudaware to discover EKS resources automatically. Read more
Access entries (recommended)
Use access entries to manage the Kubernetes permissions of IAM principals from outside the cluster. Leverage AWS documentation to ensure that:
The cluster meets one of the requirements for using access entries (platform/Kubernetes versions). Read more
Ensure that the access entry as a cluster authentication mode is enabled in AWS. Read more
Existing aws-auth ConfigMap entries are migrated to access entries (optional). Read more
aws-auth ConfigMap (legacy)
All clusters created before the introduction of access entries have the ConfigMap method enabled. Use aws-auth ConfigMap to provide Cloudaware with access to Kubernetes cluster.
Full access
Ensure you have access to the cluster and are authorized to make changes.
1. Open the aws-auth:
kubectl edit -n kube-system configmap/aws-auth
2. Add CloudAware IAM role to the ConfigMap:
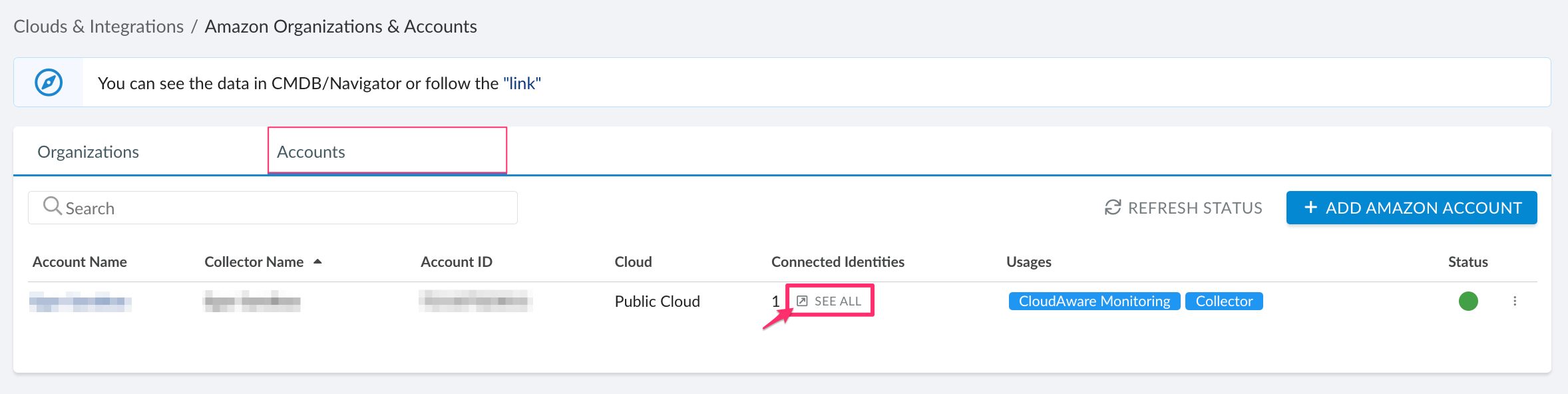
2.1. To locate CloudAware IAM role ARN, log in to Cloudaware → Admin. Find Amazon Web Services → select the tab Accounts. Locate the AWS account where access to EKS should be granted → click SEE ALL in the column 'Connected Identities':
2.2. To add assign the IAM role, add the role details to the mapRoles section of the ConfigMap under data. Use the section below if it is not present in the file:
apiVersion: v1
kind: ConfigMap
metadata:
name: aws-auth
namespace: kube-system
data:
mapRoles: |
- rolearn: <CLOUDAWARE_ROLE_ARN>
username: cloudaware
groups:
- system:mastersWHERE
<CLOUDAWARE_ROLE_ARN> – a placeholder that needs to be replaced by your Cluster Role ARN
username – the username within Kubernetes to be mapped to the IAM role (doesn't require changes)
groups – a list of groups within Kubernetes where the role is mapped to (doesn't require changes). Check Default Roles and Role Bindings for more information
Read-only access
To grant read-only access for Cloudaware, allowing the creation of ClusterRole and ClusterRole Binding in Kubernetes:
1. Create cloudaware-rbac.yaml using the section below:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: cloudaware-reader
rules:
- apiGroups: ["*"]
resources: ["*"]
verbs: ["get", "watch", "list"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: cloudaware-binding
subjects:
- kind: User
name: cloudaware
namespace: default
apiGroup: ""
roleRef:
kind: ClusterRole
name: cloudaware-reader
apiGroup: ""WHERE
ClusterRole cloudaware-reader grants read access to all resources within the cluster
ClusterRoleBinding cloudaware-binding maps the aforementioned cluster role to Cloudaware User
2. Run the following command:
kubectl create -f cloudaware-rbac.yaml 3. To map IAM users and roles to Kubernetes users in the EKS cluster, define them in the aws-auth ConfigMap which should exist after creation of your cluster. To add an IAM role to the cluster, modify this ConfigMap by adding the respective ARN and Kubernetes username value to the mapRole property as an array item. To perform the modification, run the following command:
kubectl -n kube-system edit configmap aws-authSee the example below:
apiVersion: v1
kind: ConfigMap
metadata:
name: aws-auth
namespace: kube-system
data:
mapRoles: |
- rolearn: <CLOUDAWARE_ROLE_ARN>
username: cloudawareWHERE
<CLOUDAWARE_ROLE_ARN> – a placeholder that needs to be replaced by your Cluster Role ARN
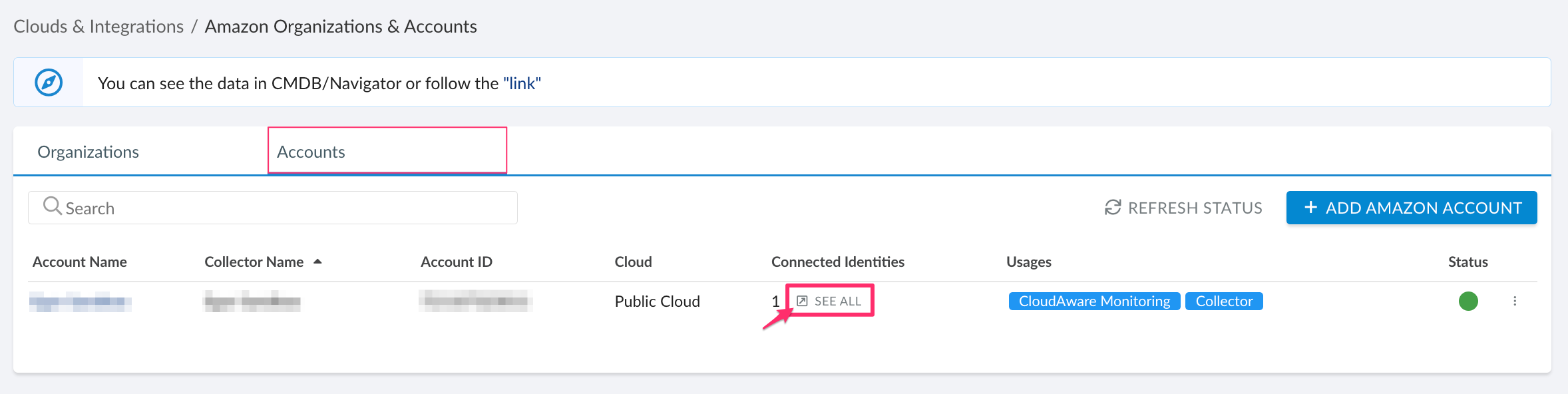
To locate your CloudAware IAM role ARN, log in to your Cloudaware account → Admin. Go to Amazon Organizations & Accounts → the tab Accounts. Locate the AWS account where access to EKS should be granted → click SEE ALL in the column 'Connected Identities':
Make sure to not remove the existing mappings in mapRoles and/or mapUsers sections. You only need to append a role for Cloudaware.
Further configuration
If the Amazon EKS Cluster is running in a private network, check this guide to install Cloudaware Breeze agent for secure connection.
EKS resources in CMDB
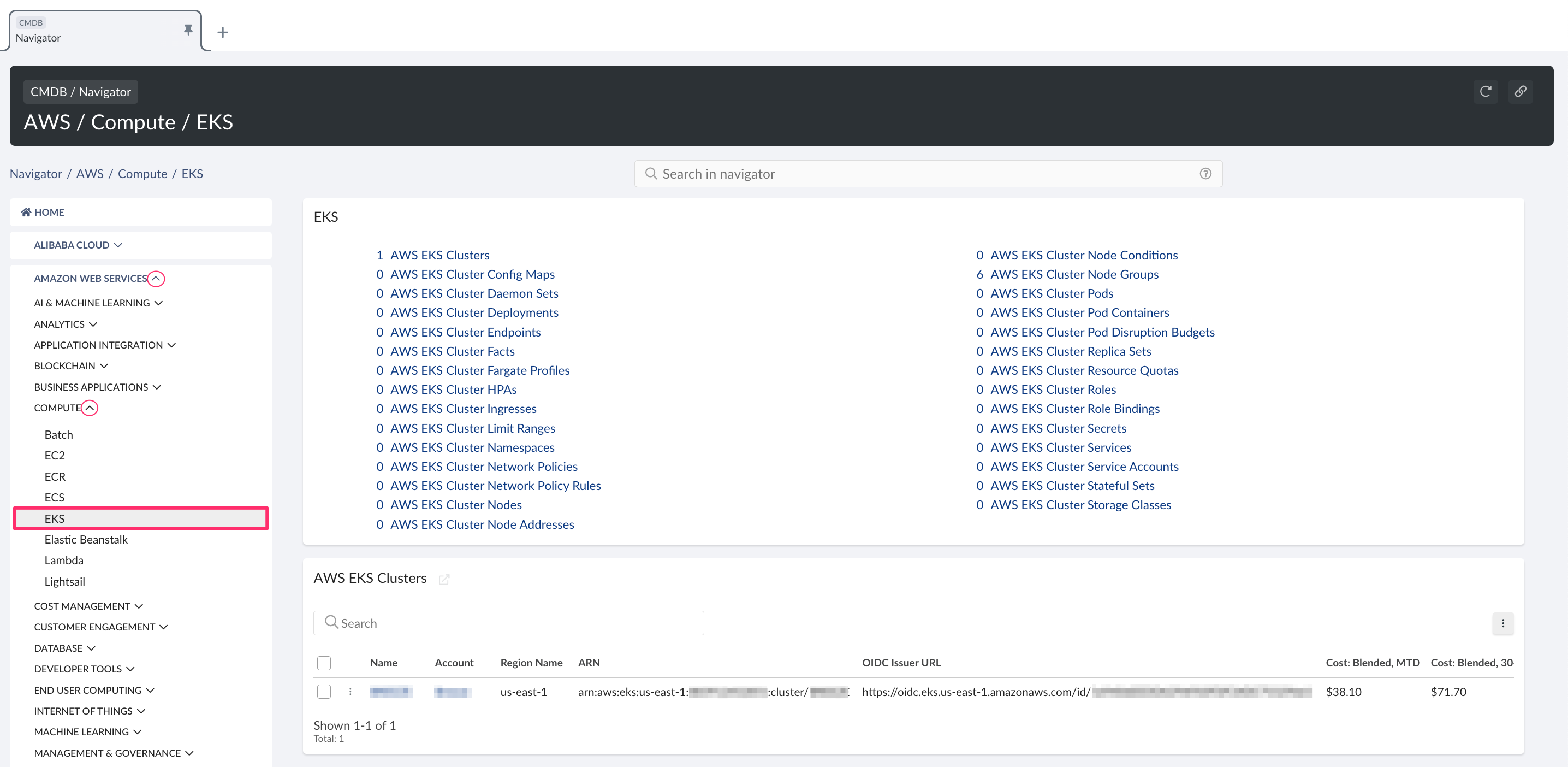
To view discovered EKS resources, go to Cloudaware CMDB Navigator → select Amazon Web Services → Compute → EKS.